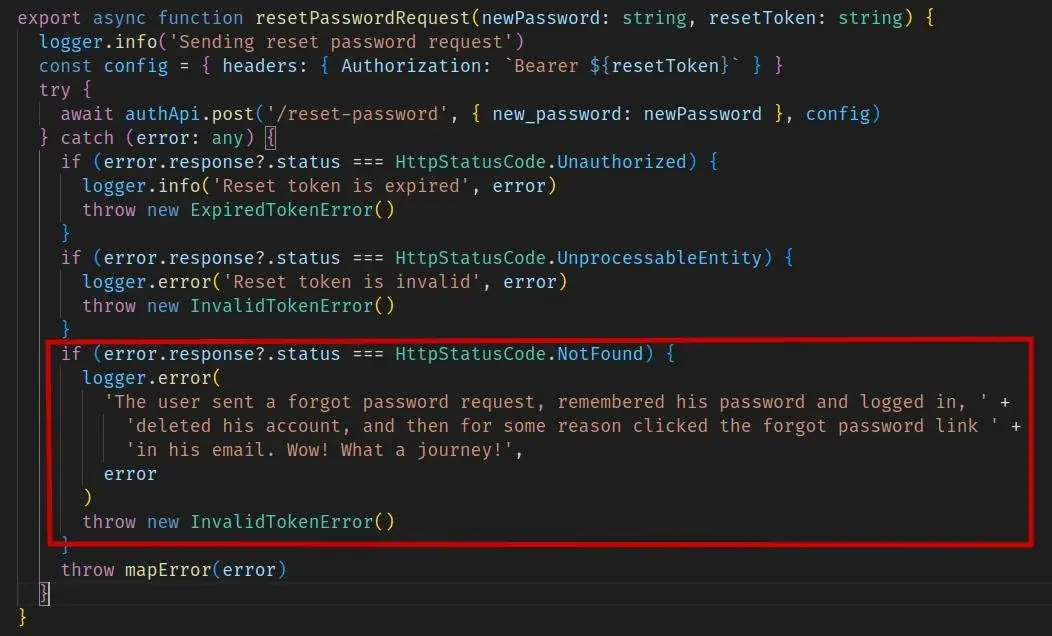
At my job, we have an error code that is similar to this. On the frontend, it's just like error 123.
But in our internal error logs, it's because the user submitted their credit card, didnt fully confirm, press back, removed all the items out of their cart, removed their credit card, then found their way back to the submit button through the browser history and attempted to submit without a card or a cart. Nothing would submit and no error was shown, but it was UI error.
It's super convoluted. And we absolutely wanted to shoot the tester who gave us this use case.