the_dunk_tank
It's the dunk tank.
This is where you come to post big-brained hot takes by chuds, libs, or even fellow leftists, and tear them to itty-bitty pieces with precision dunkstrikes.
Rule 1: All posts must include links to the subject matter, and no identifying information should be redacted.
Rule 2: If your source is a reactionary website, please use archive.is instead of linking directly.
Rule 3: No sectarianism.
Rule 4: TERF/SWERFs Not Welcome
Rule 5: No ableism of any kind (that includes stuff like libt*rd)
Rule 6: Do not post fellow hexbears.
Rule 7: Do not individually target other instances' admins or moderators.
Rule 8: The subject of a post cannot be low hanging fruit, that is comments/posts made by a private person that have low amount of upvotes/likes/views. Comments/Posts made on other instances that are accessible from hexbear are an exception to this. Posts that do not meet this requirement can be posted to !shitreactionariessay@lemmygrad.ml
Rule 9: if you post ironic rage bait im going to make a personal visit to your house to make sure you never make this mistake again
view the rest of the comments
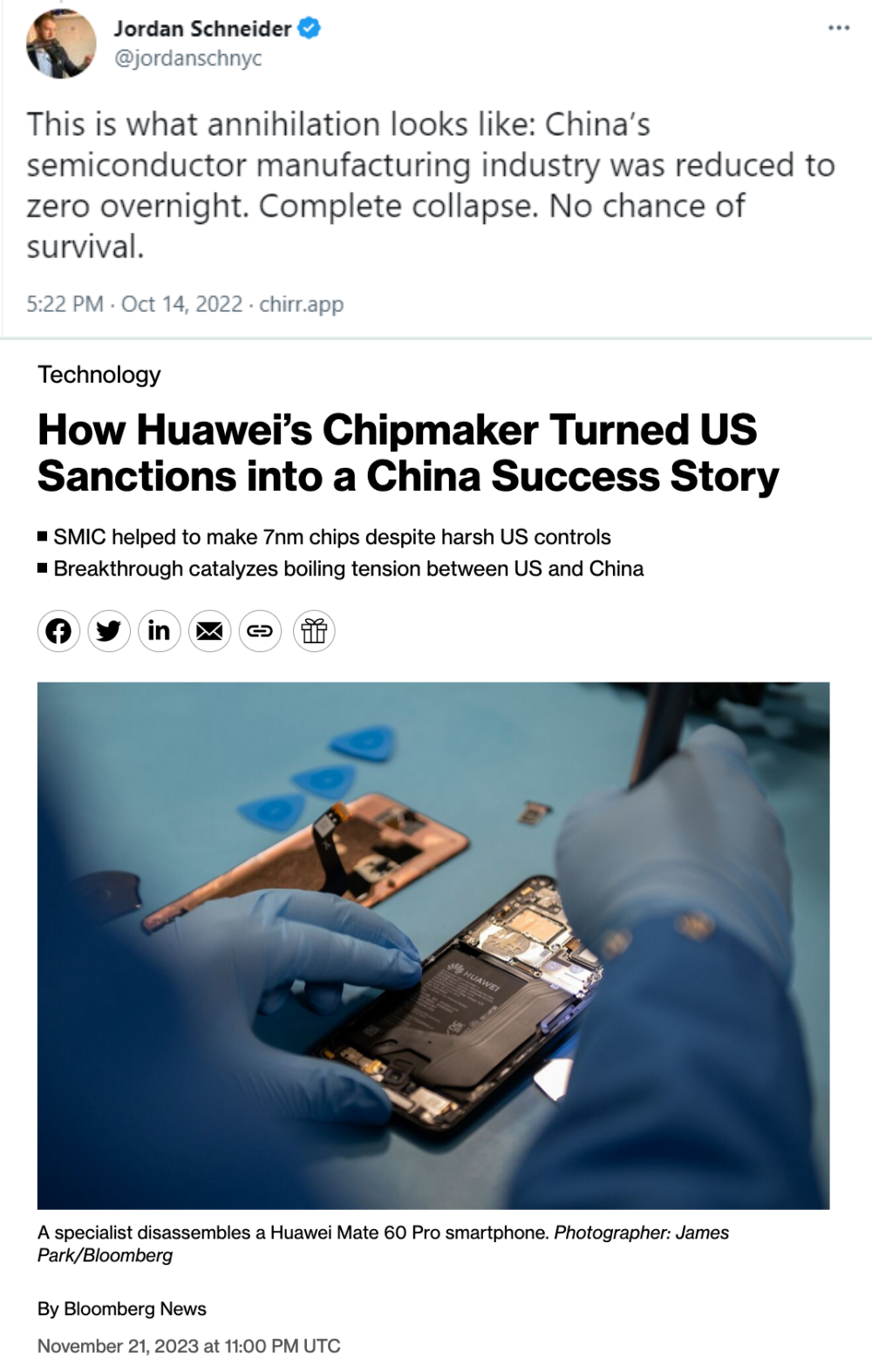
Do not rely on that. The reports are that Israel did not hack them, not that they could not. If you had a top shelf team of hardware and software backwards engineering experts who could make hay out of anything you throw at em would you go with the most popular devices in the world branded google, apple and Samsung or would you try and get the relatively unpopular outside of China huawei devices?
I’m not saying they’re not good phones, just that they’re not impossible to hack and managed to avoid it by being too small a target for anyone to do the work overcoming the differences between them and other android devices.
Yeah you’re very right but it’s something.
Not having google services and being made for a mostly Chinese market means we can, at the least, be assured they aren’t actively building backdoors like Google definitely would be.
To me it seems a rung below running a custom privacy rom. A Huawei phone with a custom privacy rom would be sweet.
Idk if that kind of thinking is helpful. The thing that sucks about security and privacy is that you have to figure out what your threat is and focus on that.
If you install a custom privacy rom on a huawei phone you might be obscuring yourself from state actors looking to gain access to westerners devices but you’re dropping yourself into the huge pool of targets for state actors (and nons !) trying to gain access to Chinese nationals devices. You’ve also made yourself really easy to clock too, since your imei says what your device is right there in the number and how many motherfuckers are strolling around Arizona with a phone you can’t buy in America in their pocket?
The other question to ask is which backdoors you want to have on your device? The obvious answer is none, no backdoors, but that’s not an option. If you are more comfortable with backdoors controlled by Chinese state owned companies as opposed to google then consider what that might mean as tension between the country you live in and China ratchet up.
Especially with the proliferation of tools for analyzing huge amounts of surveillance data, standing out because of your unique signature or if you for really real can disappear in the data field are both bad! It’s better to look like the grillman than the shadow of the hackerman.
Not trying to make a point, just rambling. Maybe make sure your Adsense profile is believably populated.
Yeah that’s the thing, I am more comfortable with Chinese backdoors.
Not in the sense of being a pro-Xi Tankie, which I basically am, but more in the sense that I don’t live in China or have any significant dealings with China. I don’t care if China spies on me.
In a world where I have to choose between Uncle Sam or Uncle Xi reading my emails, well, what’s uncle Xi gonna do to me?
To be fair I’m not that radical and Uncle Sam would find me at most list-worthy and probably not even that because I’m not that interesting but I am even less interesting to Xi, so given that choice I’d rather he’s got the keys you know what I mean?
Thank you for the write up though, upon reading my comment I wonder if I come across as argumentative and I want to stress that’s not my attitude, I appreciate your points a lot. You make good points especially about needing to blend in. I really do appreciate the effort post.
Nah you don’t sound argumentative, I probably sound argumentative.
It’s just crazy hearing people say “x is better for security”. Who’s security, what kind, under what circumstances, when and where?
Our approach to information security is very matrix when it needs to be more French connection.