196
Community Rules
You must post before you leave
Be nice. Assume others have good intent (within reason).
Block or ignore posts, comments, and users that irritate you in some way rather than engaging. Report if they are actually breaking community rules.
Use content warnings and/or mark as NSFW when appropriate. Most posts with content warnings likely need to be marked NSFW.
Most 196 posts are memes, shitposts, cute images, or even just recent things that happened, etc. There is no real theme, but try to avoid posts that are very inflammatory, offensive, very low quality, or very "off topic".
Bigotry is not allowed, this includes (but is not limited to): Homophobia, Transphobia, Racism, Sexism, Abelism, Classism, or discrimination based on things like Ethnicity, Nationality, Language, or Religion.
Avoid shilling for corporations, posting advertisements, or promoting exploitation of workers.
Proselytization, support, or defense of authoritarianism is not welcome. This includes but is not limited to: imperialism, nationalism, genocide denial, ethnic or racial supremacy, fascism, Nazism, Marxism-Leninism, Maoism, etc.
Avoid AI generated content.
Avoid misinformation.
Avoid incomprehensible posts.
No threats or personal attacks.
No spam.
Moderator Guidelines
Moderator Guidelines
- Don’t be mean to users. Be gentle or neutral.
- Most moderator actions which have a modlog message should include your username.
- When in doubt about whether or not a user is problematic, send them a DM.
- Don’t waste time debating/arguing with problematic users.
- Assume the best, but don’t tolerate sealioning/just asking questions/concern trolling.
- Ask another mod to take over cases you struggle with, if you get tired, or when things get personal.
- Ask the other mods for advice when things get complicated.
- Share everything you do in the mod matrix, both so several mods aren't unknowingly handling the same issues, but also so you can receive feedback on what you intend to do.
- Don't rush mod actions. If a case doesn't need to be handled right away, consider taking a short break before getting to it. This is to say, cool down and make room for feedback.
- Don’t perform too much moderation in the comments, except if you want a verdict to be public or to ask people to dial a convo down/stop. Single comment warnings are okay.
- Send users concise DMs about verdicts about them, such as bans etc, except in cases where it is clear we don’t want them at all, such as obvious transphobes. No need to notify someone they haven’t been banned of course.
- Explain to a user why their behavior is problematic and how it is distressing others rather than engage with whatever they are saying. Ask them to avoid this in the future and send them packing if they do not comply.
- First warn users, then temp ban them, then finally perma ban them when they break the rules or act inappropriately. Skip steps if necessary.
- Use neutral statements like “this statement can be considered transphobic” rather than “you are being transphobic”.
- No large decisions or actions without community input (polls or meta posts f.ex.).
- Large internal decisions (such as ousting a mod) might require a vote, needing more than 50% of the votes to pass. Also consider asking the community for feedback.
- Remember you are a voluntary moderator. You don’t get paid. Take a break when you need one. Perhaps ask another moderator to step in if necessary.
view the rest of the comments
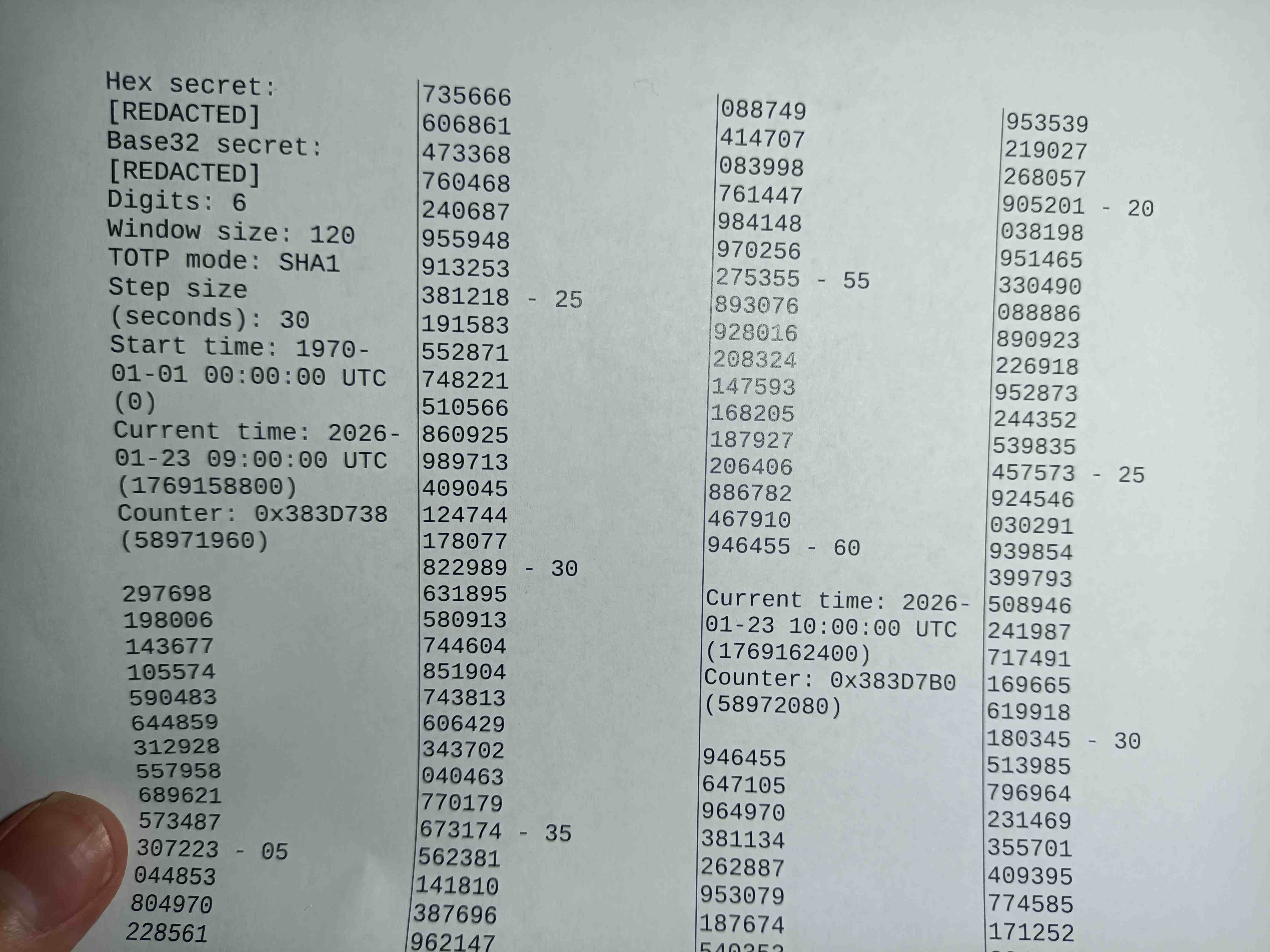
This explains the what but not the why.
Why??
I wasn't allowed to bring in my phone, which has the authenticator app. And I had to log in on a provided device. And I use 2FA.
The guy didn't even seem surprised when I asked him for current time to look up the current code, so probably this indeed was within the expectations.
"You can have the password printed out" - part of the instructions
Or they could just give a you a hardware token like Thales does.
High security devices like government computers will instantly bluescreen if you plug anything into the USB ports. And then you’ll get a call from IT to speak with your manager, who will (at best) give you the single largest chewing out of your life or (at worst) have multiple big dudes with handcuffs waiting in their office.
And yes, this includes hardware tokens.
Thales also does key fobs that generate OTPs
But why couldn't you bring a phone where you were going, and why did you have to log into a strange device?
What were you doing?
High security stuff where anything electronic is a spy device until thoroughly proven otherwise. You're not going to get a specific answer unless OP is an idiot.
I'm going to brainstorm a few ideas because I'm really curious about this. It sounds like an exciting life to live.
Would these be examples of the following?
These are the only things I can think of. For any regular job, I don't understand why they wouldn't just give you a hard token. One of those things that you put on a key ring, which shows you a time-based second factor string of numbers on a little LCD screen.
I had one of those and I was not doing anything sensitive. I was just an environmental educator working for the state government and I had to use it to login to the state laptop to submit my time sheets.
On the other hand, if they won't give you a hard token, because they're worried you might bring your own device that looks like a hard token and replicates their hard token except with additional spy hardware, I'm not sure why they are allowing you to log into something on that laptop.
Or if they do expect you to log into something on that laptop, I don't understand why you'd have to come up with your own custom solution rather than them have some kind of system that everybody uses.
I like the ideas here, so much so that I feel bad for giving you a disappointing answer: exam.
No own electronic devices in the exam room. That included everything, phones, watches, calculators and they also specifically mentioned "hearing aid" while giving out all instructions verbally.
Perhaps if there was someone it applied to they wouldn't but...
And I had to log into our system to take it, which uses TOTP 2FA. An odd situation. Since the only other thing from clothes being allowed was a pen and paper with password (if needed), here we are.
But one real world example I heard from someone is no unapproved devices being brought into the server room.
Sorry, nothing interesting going on in here.
That's exactly something a secret shadow government spy consultant agent would say.
Thanks for sharing! So did everyone have to print out their time based authentication codes, or were there other 2fa options, or do some students just not have 2fa enabled?
So fascinating, seriously.
I didn't notice, and I don't tend to talk to people, so no idea.
The person next to me didn't use 2FA, that's all I know.