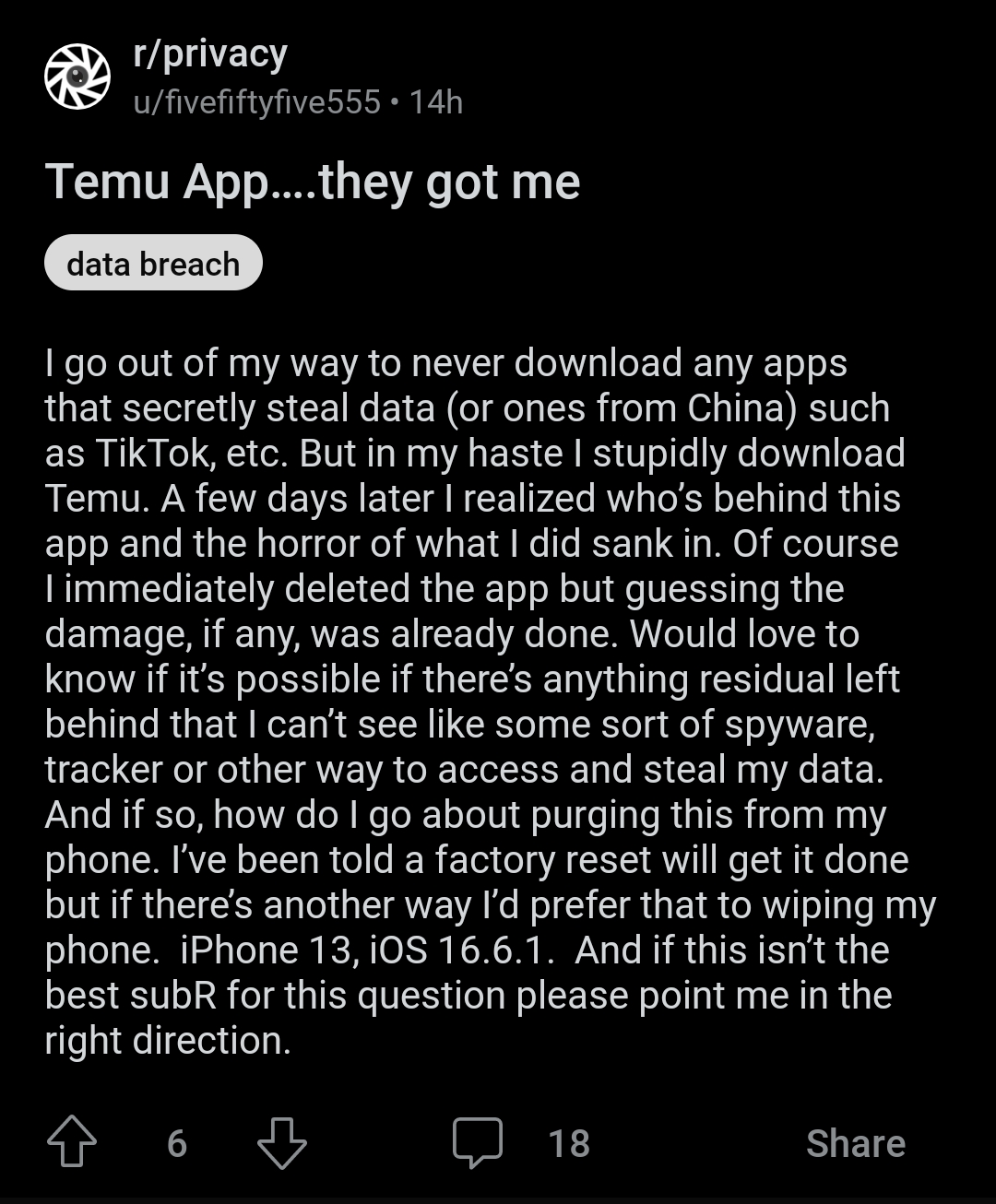
the_dunk_tank
It's the dunk tank.
This is where you come to post big-brained hot takes by chuds, libs, or even fellow leftists, and tear them to itty-bitty pieces with precision dunkstrikes.
Rule 1: All posts must include links to the subject matter, and no identifying information should be redacted.
Rule 2: If your source is a reactionary website, please use archive.is instead of linking directly.
Rule 3: No sectarianism.
Rule 4: TERF/SWERFs Not Welcome
Rule 5: No ableism of any kind (that includes stuff like libt*rd)
Rule 6: Do not post fellow hexbears.
Rule 7: Do not individually target other instances' admins or moderators.
Rule 8: The subject of a post cannot be low hanging fruit, that is comments/posts made by a private person that have low amount of upvotes/likes/views. Comments/Posts made on other instances that are accessible from hexbear are an exception to this. Posts that do not meet this requirement can be posted to !shitreactionariessay@lemmygrad.ml
Rule 9: if you post ironic rage bait im going to make a personal visit to your house to make sure you never make this mistake again
view the rest of the comments

That's not protection, and worse its giving you a false sense of security. I don't make my recommendations because I hate tech, but because (from a security posture) the attack surface is so large it is impossible to verify it cannot be used against you, and the consequences of that mistake are life-altering.
A SIM merely says you are Authorized to use the network. The phone still makes connections to the cellular network. All phones on the market allow emergency calls even without a SIM card.
Both your cellular chip and your WiFi chip broadcast their unique MAC address to every router/tower they see, and all of this information is logged.
Just like a burner phone, police can get the location data from the carrier and towers, and use that to trace where that phone went. If you brought that phone near other devices, those devices or your own location can be deduced.
You see this over and over: Big Protest ➡ Police Geofence warrant ➡ Cell logs ➡ Arrests. Given the criminalization of protests this will become the norm. If you want to get rid of advertising, many of the suggestions here are fine. But none of them go far enough to protect you beyond that, even from Big Tech surveillance.
True that for just using a sim card less phone.
However
GOS airplane mode disable any connection to the cellular network. If I'm wrong if love to hear some evidence to the contrary.
It's not that we are wrong or right, we cannot verify. That is the danger. In a high security environment I treat everything as suspect until proven otherwise. However when you do not use technology you categorically exclude an entire attack surface, and it is extremely simple to get right.
Sure , not using a phone is of course the best option. If that is an option. For most people, activist or criminals of any kind. Not usually an option.
You can at least verify the Foss code. Or trust the people that verify it.
I'm not responding to be mean, so I'm sorry if this feels like bullying. I've had friends and comrades arrested and jailed, and I don't want anybody falling into that trap if it can be easily avoided. I'm trying to point out the Ideologies (*sniff* ), the things you don't know you know, so that you can operate a much stronger security posture.
), the things you don't know you know, so that you can operate a much stronger security posture.
The first Ideology is using the same device in both high and low security environments. Don't. Use multiple devices and compartmentalize aggressively. In security posture, you are only as secure as your weakest point. This is why those "criminals" use a different burner phone. Using a single device to communicate with grandma and radicals is a recipe for baking and arrest. I consider a low-security place where I shitpost and goof off, but I absolutely do not engage in any
a low-security place where I shitpost and goof off, but I absolutely do not engage in any  here because it would be trivial to trace it to me. Same with my regular cell phone, which I text grandma baking recipes but never use it during protests.
here because it would be trivial to trace it to me. Same with my regular cell phone, which I text grandma baking recipes but never use it during protests.
The second Ideology is thinking you are excluded from those so called "activists and criminals" while participating in very leftists and public online spaces. I guarantee and
and  watch both Lemmygrad and Hexbear as I type this, and they don't give a single
watch both Lemmygrad and Hexbear as I type this, and they don't give a single  ! Rude! To them we are all being gay and doing crime. Have fun giving them
! Rude! To them we are all being gay and doing crime. Have fun giving them  but you deliberately never go beyond that.
but you deliberately never go beyond that.