OpenWrt
OpenWrt news, tools, tips and discussion. Related projects, such as DD-WRT, Tomato and OpenSAN, are also on-topic.
Rules
-
Stay on topic: All posts should be related to OpenWrt and related projects, including DD-WRT, Tomato, OpenSAN, and more!
-
No offensive or low-effort content: Don't post offensive or unhelpful content. Be nice - keep it civil and friendly!
-
Describe images/videos, no memes: Please include a text description when sharing images or videos.
-
No self-promotion spam: Active community members can post their apps if they answer any questions in the comments. Please do not post links to your own website, YouTube, blog content, or communities.
-
No reposts or rehosted content: Share only the original source of an article, unless it's not available in English, behind a paywall or requires logging in (like Twitter). Avoid reposting the same topic from other sources.
-
No editorializing titles: You can add the author or website's name if helpful, but keep article titles unchanged.
-
No piracy: Do not share links or direct people to pirated content.
-
No unauthorized polls, bots, or giveaways: Do not create polls, use bots, or organize giveaways without first contacting mods for approval.
-
No affiliate links: Posting affiliate links is not allowed.
view the rest of the comments
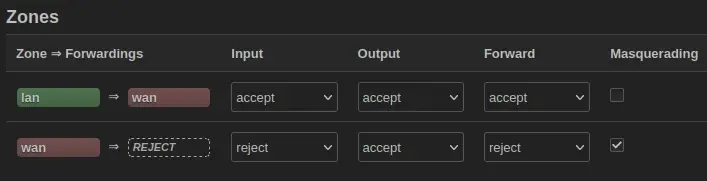
have clicked the add button at the bottom of the zones, found the below. A look at the current zones show that LAN -> WAN is how you get out and WAN -> REJECT is the WAN -> LAN side.
So what your doing is allow all traffic in, out and forwarded of LAN
But reject any in and forward from WAN to LAN, as the traffic leaves the WAN interface masquerade it as the WAN IP
This section defines common properties of "this new zone". The input and output options set the default policies for traffic entering and leaving this zone while the forward option describes the policy for forwarded traffic between different networks within the zone. Covered networks specifies which available networks are members of this zone.
The options below control the forwarding policies between this zone (this new zone) and other zones. Destination zones cover forwarded traffic originating from this new zone. Source zones match forwarded traffic from other zones targeted at this new zone. The forwarding rule is unidirectional, e.g. a forward from lan to wan does not imply a permission to forward from wan to lan as well.
I don't understand this one. Wouldn't this then reject any connection to the router from the internet? Say you have a server behind the router that is port forwarded. If you have
Input: rejectonwan, wouldn't this then mean that the router just drops any request to the server as that would be an input originating on thewaninterface destined for the router?This is a great way to explain the masquerade setting! Thanks!
Thats how my setup looks, I do have about 7 NAT rules also and they work fine
Do you not know the answer to my question, or did you perhaps misunderstand it? You seem to have skipped over the whole comment 😆
in short, no I dont know how the firewalling works.
So a read of the wiki has what I thought
all as default settings, NAT is applied after the zone rules. So even though the zone will reject INPUT, a NAT rule will allow it.
Does that help?
I don't think this is correct. NAT doesn't "allow" connections -- It just masquerades the source IP as that of the router. For WAN connections to be accepted, conntrack must see them as related to connections that were initiated by the router, or by a device on the LAN (assuming, of course, that conntrack is enabled, which, in my case, it is).