view the rest of the comments
Software Gore
Welcome to /c/SoftwareGore!
This is a community where you can poke fun at nasty software. This community is your go-to destination to look at the most cringe-worthy and facepalm-inducing moments of software gone wrong. Whether it's a user interface that defies all logic, a crash that leaves you in disbelief, silly bugs or glitches that make you go crazy, or an error message that feels like it was written by an unpaid intern, this is the place to see them all!
Remember to read the rules before you make a post or comment!
Community Rules - Click to expand
These rules are subject to change at any time with or without prior notice. (last updated: 7th December 2023 - Introduction of Rule 11 with one sub-rule prohibiting posting of AI content)
- This community is a part of the Lemmy.world instance. You must follow its Code of Conduct (https://mastodon.world/about).
- Please keep all discussions in English. This makes communication and moderation much easier.
- Only post content that's appropriate to this community. Inappropriate posts will be removed.
- NSFW content of any kind is not allowed in this community.
- Do not create duplicate posts or comments. Such duplicated content will be removed. This also includes spamming.
- Do not repost media that has already been posted in the last 30 days. Such reposts will be deleted. Non-original content and reposts from external websites are allowed.
- Absolutely no discussion regarding politics are allowed. There are plenty of other places to voice your opinions, but fights regarding your political opinion is the last thing needed in this community.
- Keep all discussions civil and lighthearted.
- Do not promote harmful activities.
- Don't be a bigot.
- Hate speech, harassment or discrimination based on one's race, ethnicity, gender, sexuality, religion, beliefs or any other identity is strictly disallowed. Everyone is welcome and encouraged to discuss in this community.
- The moderators retain the right to remove any post or comment and ban users/bots that do not necessarily violate these rules if deemed necessary.
- At last, use common sense. If you think you shouldn't say something to a person in real life, then don't say it here.
- Community specific rules:
- Posts that contain any AI-related content as the main focus (for example: AI “hallucinations”, repeated words or phrases, different than expected responses, etc.) will be removed. (polled)
You should also check out these awesome communities!
- Tech Support: For all your tech support needs! (partnered)
- Hardware Gore: Same as Software Gore, but for broken hardware.
- DiWHY - Questioning why some things exist...
- Perfect Fit: For things that perfectly and satisfyingly fit into each other!
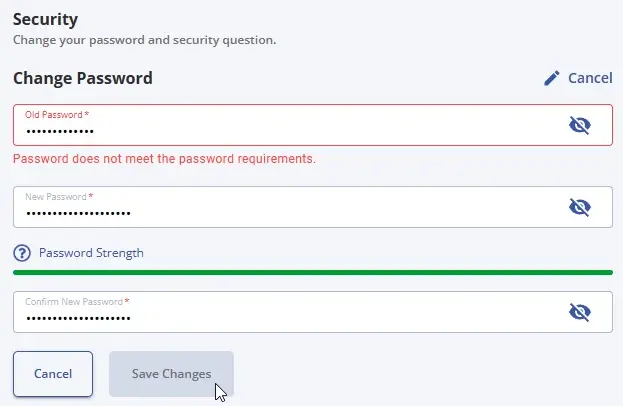
Whatever site that is, make sure you use a burner email, burner pw (if you get it to work) and joe doe contact info.
To me it looks like their frontend guy just copy/pasted the password field with all validation over without thinking twice. I wouldn’t say this speaks to their general security competence.
While that may be true(copy/🍝), it implies that their code quality and QA process is broken and some of the most important fields/data are not being closely looked it. It certainly DOES speak to their overall security competence.
Eh, I can see how it's missed by testing. The tests probably cover testing non-compliant passwords failing and compliant passwords passing. They were probably updated at the same time the password compliance was updated.
Missing an edge case like this isn't good, but it's not that uncommon.
Again, a basic code quality issue. If they missed this basic functional code issue, what else did they miss that is exploitable….
Could also be backend validation is broken, so FE just shows the user something useful rather than waiting for backend to reject and show a generic error message.
Found the FE dev. I think there is a JavaScript library for finding ways to blame the backend.
I mean... I've been both. I have had to punt a problem that caused FE anguish because the project is old, not the priority, and hard to make changes to.
I've also been the FE that was told that they are aware of the problem, and can't get to it for a month, so we need to at least make the UI surface the error in a better way so that the user can go to support for manual intervention.
That would be actively malicious. I don’t know how anyone could get the idea to just show “something” if the backend sends a generic error message.
Huh? If backend has incorrect validation on the old password string, and returns an error message like "invalid password" without specifying if it's the old or new password, that's not particularly helpful for front end. And that's pretty common for an API response not to have fine grain details.
The UI is capable of validating up front before the service request, assuming they know the exact validation rules BE uses.
Or the FE just fucked up. Both are plausible.
Burner PW?
Just use a manager.