this post was submitted on 14 Sep 2024
1621 points (99.0% liked)
Technology
82414 readers
3365 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related news or articles.
- Be excellent to each other!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, this includes using AI responses and summaries. To ask if your bot can be added please contact a mod.
- Check for duplicates before posting, duplicates may be removed
- Accounts 7 days and younger will have their posts automatically removed.
Approved Bots
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
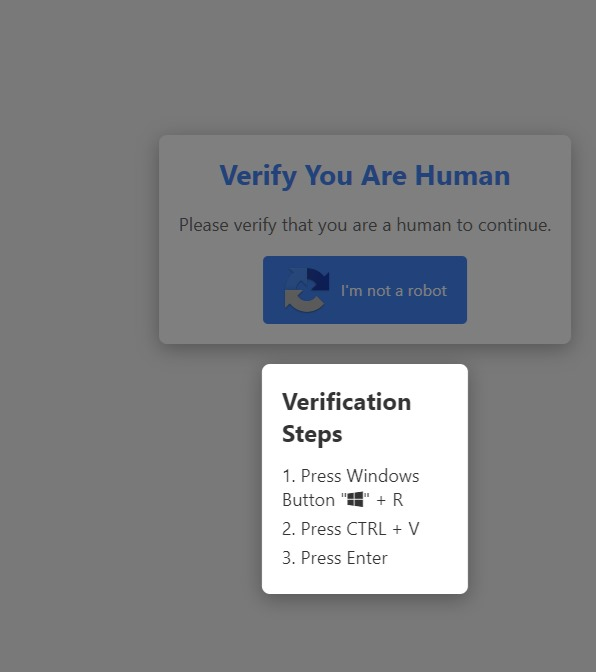
Your story reminds me of something that my bank started doing. I got a robocall about something to do with my credit card, and the voice said to verify using x and y using my keypad, I think it was day/month/year of birth or something and I immediately noped out of the call. I hit all the wrong buttons until it got me to a person and I ripped them apart, and their supervisor for basically training their userbase to answer security questions given by an automatic voice on the other end of the line with no way to verify who is calling.
You can spoof your caller ID, you can get a text to speech robocall bot with DTMF recognition and just spam call a whole area where the bank operates and gather a bunch of personal information because it sounds just like the bank and there's no way to prove who called.
What a crock of shit. It's a security nightmare.
I did call my bank after at a known valid number, verified them as they verified me, and there was something going on, so the call was legit, and totally unacceptable.
These clowns want us to trust them completely, and give us no reason to do so, but they want us to bend over backwards to validate ourselves. Fuck that.
Yeah, I really hate the state of the banking industry. IMO, all banks should:
So many banks are super insecure, and I'm absolutely willing to jump through a lot of hoops to make my accounts more secure. That's why I'm with my current bank, it's one of the few that can actually be somewhat secured, and I left my last bank because they removed email 2FA (I trust my email much more than I trust the SMS network).
Well, I have no arguments with what you've said. I think security keys/FIDO tokens should be more prevalent too. Otherwise this is 100% correct and I feel the exact same way.
Yeah, I tried using a security key, but the only financial institution that looked halfway interesting that supports security keys was Vanguard, and they fall back to SMS, so it's functionally useless.
I have zero problem using security keys, but if it only works for a handful of inconsequential services, why bother?
I prefer security keys. At work I use a yubikey, and I have Google's security keys for my personal stuff. I tend to use totp as a backup.
For everything not banking, it's great, I agree. I still prefer my security keys to everything. It's hard to duplicate a digital key when it only exists on protected storage on a physical device, where that key never exists outside of that physical device.
In case anyone doesn't know: FIDO works using a pair of asymmetric digital keys, the public key is sent to the remote site, and only the private key can decrypt anything encrypted by the public key. So a challenge (usually some mathematical calculation, not sure), is encrypted by the site/service that is handling the login, it sends over the encrypted request, which is passed, in it's entirety to the fob. The fob requires a physical activation to process the challenge (usually a touch, but some require a fingerprint). The challenge is then decrypted, processed, the response is encrypted, and sent to the site for login, which decrypts the response with the public key, and compares the result to the result of the challenge that was sent.
There's no part of this that can really be compromised. An eavesdropper can obtain the encrypted challenge (unable to be decrypted in any reasonable manner), and the response/public key... The public key isn't useful, and the response is only valid for that specific login because there are aspects of the challenge that are unique per login.
All information in flight is unreadable nonsense. The only unique information to the key that is sent anywhere is the public key, which is supposed to be public.
Totp has the vulnerability of needing to relay the seed, usually by QR code. The only vulnerability there is when you set it up and the seed is shared to you, it can be intercepted. If that seed is stored anywhere that becomes compromised, then it becomes meaningless. It can be mined from an authenticator, or captured in flight.
Both of these are better than alternatives. Email/sms codes can be intercepted, either by an administrator or by an internet relay, or by sim duplication, etc. You know that already.
I don't hate totp, I just recognize the faults in it.
There's problems with physical security keys too, mainly in the fact that, if you lose the fob, you're screwed. So it's recommended to have a backup. Either in the form of a second fob, which is setup for all the same accounts which is stored securely, or in the form of another authentication method like totp.
Personally, I use a backup FIDO key for my accounts whenever possible. I also have a password manager that can store my totp so everything is in a single vault. If the vault is compromised then I'm screwed though... 90% of my accounts use a password reset email which is not stored in my vault. Only two things are not in my manager: that recovery email login (secured by my Fido key) and my bank (obviously also the vault login).
At work, I use the yubikey for everything that supports it, with totp as backup in my work's duo authenticator account (duo is also setup to use my yubikey). So it's all Fido/totp.
The only service I really want to use my security keys with that doesn't support it, is my bank account.... I suppose, also my government stuff, but almost all of that is informational. I can't really make changes to my government stuff from their webpages. It's generally just the government telling me things about my tax returns and whatnot (all SMS secured).
I hate the trend of companies requiring an app for 2FA... Something that's not totp, but similar. You have a specific authenticator app for a single service on your phone only and it's not great.... Obvious examples include steam and Blizzard. Fuck that. I hate it. Go away. Give me normal MFA options.... Dick.
I've ranted enough. Back to work for me.
Same, I wish I could use security keys everywhere. I have an older YubiKey (version 4?), and it doesn't get used because only like 2 services I use support it, and those support TOTP. I would switch all of my banks today if I could.
So I stick with TOTP because it's "good enough" and works everywhere. If I had more than a small handful of services that worked with my YubiKey, I'd absolutely bring it with me everywhere.
Yeah, it totally sucks. I have decided to just not install apps if I can get away with it, which is nice because tons of them don't even work with how my phone is set up (GrapheneOS, no Play services). So I'm going to be a thorn in their side as long as I can. They should just support TOTP since it's already ubiquitous, and ideally also support security keys.